The core concept that blockchain solves is primarily focused on enabling private and secure communication between two parties. This was primarily driven by the first implementation of blockchain technology is for a Digital Currency, and that is no coincidence because Money after all is a communication technology, because exchange of money relies on communication.
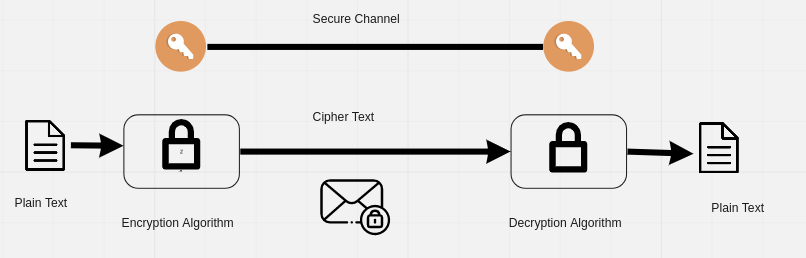
The fundamental objective of cryptography is to enable two parties to communicate over an unsecure medium. This is achieved by encrypting a Plain Text from the sender to form a Cipher Text that can only be decrypted by the receiver, with whom the sender shares a secret. Third parties may intercept the channel which is used to transport the Cipher Text, but the text doesn't have any meaning to it, so it doesn't matter whether the channel is secure or not.
A cryptosystem should be secure even if everything about the system, except the key, is public knowledge. The key is the only asset in cryptography that has to be kept secret and protected from intruder attacks.
Auguste Kerckhoffs
In What is Blockchain I discussed the basics of a Hash Function which is one of the examples how Cryptography is used within Blockchain, used to create links between blocks.
Cryptography is also used in consensus algorithms such as proof-of-work, which basically exploits the hashing power of the computing systems that form the blockchain network. Digital signatures are used to sign and verify events such as transactions. Asymmetric key cryptography is a core concept in blockchain applications that gives identity to the participants of the network or can prove the ownership of assets.
Understanding Classical cryptography
In order to understand how cryptography is used within Bloclchain Technology, its important to gain a broad understanding of encryption and how it has evolved over the years.
In a classical encryption scenario, a Plain text message maybe Encrypted using a secret key that is shared with another user or third party over a secure channel. The party that wants to read the text will decrypt the cipher text using the secret key, which will return the original Plain Text.
The key is private, and the encryption and decryption algorithms are made public because it is impossible to decrypt the cipher text without the key.
Two types of operation are used to transform plaintext to ciphertext: substitution and transposition. Both of these techniques ensure that the operation is reversible, and therefore they could be used in encryption algorithms.
Substitution
Encryption method in which the characters in plaintext are replaced by other characters in a fixed manner. The simplest example of a substitution cipher is Caesar's cipher, where plaintext letters are substituted by shifting the alphabet by three places: the letter A is replaced with D, B with E, and so on. The obvious problem with this cipher is that the method is fixed and that there is no key involved.
A variant of Caesar's cipher, called the Shift cipher, was introduced, where the amount of shift from the plaintext to the ciphertext varies, and this amount of shift can act as a key. Although this solved the immediate problem, it wasn't practical enough as the key could be guessed with a brute-force or an exhaustive search attack.
The polyalphabetic cipher was the next stage in the evolution of ciphers. This cipher introduced a number of substitutions at different positions in the message.
Transposition
Encryption method where the positions of plain text letters are shifted according to a known system. Only the order of plain text is altered. All the letters of the plain text remain the same.
The Rail Fence cipher and the Route cipher are two well-known transposition ciphers. This kind of cipher technique could be decrypted by finding the transposition patterns using anagramming.
Symmetric Key Cryptography
a key-based cryptography whose algorithms use the same keys to perform encryption of plaintext and decryption of the ciphertext. These keys are shared between two parties over a secure channel. Any participant owning the shared key can perform both encryption and decryption operations on the data. A symmetric key cipher can either be stream encrypted or block encrypted.
Symmetric key cryptography doesn't play any significant role in blockchain-based applications. However, it will provide a better insight into key-based cryptography before we look into asymmetric cryptography.
Stream Cipher
Using symmetric key cryptography. Each plaintext character is encrypted one at a time, like a stream, to create the ciphertext.
A keystream, or stream of characters, is used to encrypt the plaintext characters. A pseudorandom string is used, which acts as a keystream. This pseudorandom string is generated from a random seed value using digital shift registers.
The seed used is the secret key, which is also used to decrypt the created ciphertext.
For a stream cipher to be secure, its pseudorandom generator should be unpredictable, and its seed value used to generate the keystream should never be reused to reduce the possible attacks. Stream ciphers are generally faster than block ciphers and have low hardware requirements.
Block Cipher
A block cipher is a cipher in which encryption is performed on a fixed-length block of characters from the plaintext. This cipher technique is widely used to implement encryption on bulk data. The usual block sizes are 64 bits, 128 bits, and 256 bits. For example, a 64-bit block cipher will take 64-bit plaintext as input and give out 64-bit ciphertext.
The plaintext will pad some of the blocks in case some of the plaintext falls short of filling a block. Because the keys used in block ciphers are considerably long, they are robust against brute-force attacks. These ciphers are also the building blocks of other cryptographic protocols, such as hash functions and random number generators.
Some examples of popular block cipher algorithms include:
- Data Encryption Standard (DES)
- Advanced Encryption Standard (AES)
- International Data Encryption Algorithm (IDEA)
- Blowfish
Asymmetric Key Cryptography
Asymmetric key cryptography is a widely used encryption technique in modern cryptography. It has a lot of applications other than encryption. It is also commonly used in several elements of blockchain technology.
Symmetric key cryptography uses a shared key for both encryption and decryption. The biggest problem with this is that the shared key needs to be exchanged between participants over a secure channel, which can be quite hard to achieve. This can defeat the entire objective of encryption if we have a secure channel for communication in the first place.
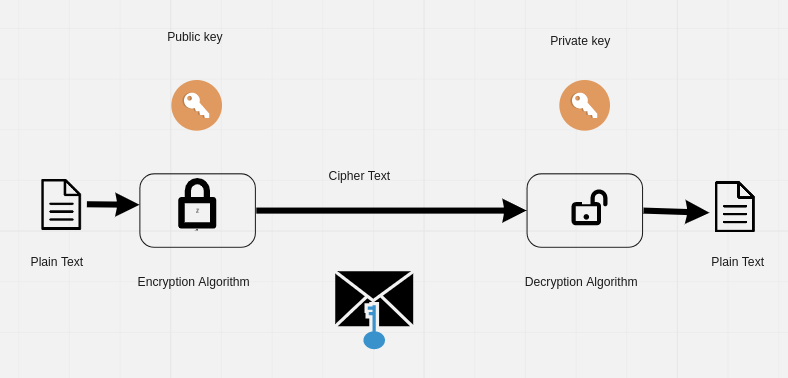
This is where asymmetric key cryptography comes in. It uses a pair of keys called a public/private pair. The public key is constructed from the private key and can be freely broadcasted to other users.
Public-key algorithms enable the creation of a public key from a randomly generated private key. The created public key could not be used to infer the private key. In other words, the creation of the public key from the private key is a one-way process. This is the concept on which the security of public-key cryptography relies. The public-key algorithm not only performs encryption, but also provides authentication functionality.
The holder of the private key can use this key to authenticate to a system that is aware of the user's public key.
asymmetric key algorithms can also be used to provide authentication. One application of this mechanism is digital signatures: only users with the private key could sign a message, and anyone possessing the public key could verify the authenticity of the message. Digital signatures could be used for non-repudiation as well.
Blockchain applications, especially crypto currencies, make use of digital signatures to sign transactions using a private key to prove ownership.
blockchain technology relies mainly on asymmetric cryptographic algorithms such as:
- Diffie-Hellman key exchange
- DSA
- ElGamal
- RSA
- Elliptic-curve cryptography (ECC)
The strength of a public-key cryptography system depends on how feasible it is to infer the private key from the publicly available information about the key. Although it is infeasible, it is not impossible, and security relies solely on the key size and key generation mechanism. Asymmetric keys are not widely used due to their complexity and the time it takes to encrypt/decrypt large files. They are commonly used in digital signatures or key exchange mechanisms rather than in encryption protocols.
All asymmetric key algorithms are based on a number theory problem that ensures the characteristics required for key generation and the encryption and decryption processes. Based on different ways of solving the mathematical problem in number theory.
Three main asymmetrical public-private key generation algorithms in blockchain:
- prime factorisation
- discrete logarithm
- elliptic-curve.
Digital Signatures
A digital signature is a method of providing proof of ownership of digital documents. Public-private key cryptography is widely used in the field of digital signatures due to their asymmetric key property. The owner can use the private key to sign a message or document, and the verifier can verify their ownership using the public key, which is distributed to everyone.
The process is similar to the handwritten signatures used in the offline world, where an owner of an asset can use their signature to perform any action on that asset and anyone can verify the signature by comparing it with a signature that was used previously.
Digital signatures could be used as a mechanism for ensuring the authenticity, non-repudiation, and integrity of an action.
Cryptographic Hashing
A cryptographic hash function is a type of function that maps arbitrary sized data to a fixed size string called a hash. Hash functions possess certain properties that make them ideal for use in cryptography.
Hash functions are widely used in hash table data structures. A hash table stores the data in a key-value pair. Hash tables are used when large keys need to be converted into smaller keys using a hash function, and then the values are mapped to these smaller keys. This makes the mapping of key to value quite easy, and this could be achieved in O(1) time complexity. This is due to the fact that hash functions have a constant time complexity.
hashing is the backbone of blockchain architecture, and it has several properties that make it really valuable and ideal for blockchain implementation.
Hashing is used in blockchain to create a unique identity string for each block by computing its hash value. Each block will maintain the hash value of the previous block and thus form a chain of blocks. Hashing provides integrity to the blocks of the blockchain ledger.
Hashing algorithms
Hashing is an important concept in blockchain and has a huge role in the functioning of a blockchain application. The applications of hash functions range from minor blockchain implementations, such as creating a digest for a large amount of data, to major implementations, such as maintaining the integrity of the blocks in the chain.
Hash functions are also used in Proof of Work consensus algorithms to solve the Byzantine failure problem.
Categorisation of hashing algorithms are typically based on their implementation, digest size amongst other features.
Messages Digest
One of the most popular hashing algorithm groups used during the early 1990's.
a fixed size numeric representation of the contents of a message, computed by a hash function. A message digest can be encrypted, forming a digital signature. Messages are inherently variable in size. fixed size numeric representation of the contents of a message. 128-bit hash functions, and md4 and md5 are its variants.
Many vulnerabilities have been detected in the function since its adoption. However, these functions are still used to create file digests to ensure their integrity.
The message digest is sent with the message itself. The receiver can generate a digest for the message and compare it with the digest of the sender. The integrity of the message is verified when the two message digests are the same. Any tampering with the message during transmission almost certainly results in a different message digest.
Secure Hash Algorithms (SHA)
a set of algorithms developed by the National Institutes of Standards and Technology (NIST) and other government and private parties.
SHA-0 is the first version of the SHA algorithm. In 2004, several weaknesses were exposed in this algorithm, resulting in the creation of a stronger version of SHA-0 called SHA-1. In 2005, an attack on SHA-1 reported that it would find a collision in fewer hashing operations.
SHA-2 was created to overcome SHA-1's vulnerabilities, and it could be implemented with a digest size of 224, 256, 384, and 512 bits. SHA-2 is a widely used standard in modern cryptographic applications. Bitcoin uses the SHA-256 variant as a hashing algorithm to solve proof-of-work puzzles.
SHA-3 is the latest family of functions with 224-, 256-, 384-, and 512-bit variants.
Public and Private Keys
The corner stone of cryptography in cryptocurrency are Public and Private keys. private and public keys make decentralization possible.
- Private keys are used to initiate a transaction.
- Public keys are used to verify transactions.
Public key cryptography is also known as asymmetric encryption or trapdoor functions where information is encrypted and decrypted. The idea behind PKC is that it takes an immeasurable amount of time to solve the mathematical function, but it is so easy to calculate and verify it.
Private Keys
Used to digitally sign cryptocurrency transactions.
It is vitally important that private keys are kept private and not shared with anyone whatsoever. If someone has your private key, he/she can use it to access your crypto wallet.
Public Keys
Public keys are used to encrypt a transaction before it occurs and then to sign the transaction after it is verified. Only after the transaction is signed with a public key, it can be added to the blockchain and let others know that the blockchain has been updated.
Public keys can be shared without being vulnerable. People cannot access your assets through your public keys.
Conclusion
Each cryptographic primitive that is used with blockchain technology has a distinct role. Hash functions and digital signatures are two concepts of cryptography that are extensively used with blockchain.
Cryptography is mainly used in the consensus and application layers of the blockchain. A hashing algorithm is mainly used to create block identity, ensure the integrity of the blockchain, and also acts as a key ingredient of consensus algorithms, such as Bitcoin's Proof of Work. The digital signature, on the other hand, deals with the application layer, where it is used to validate events by embedding them in transactions.
- What is this Directory.Packages.props file all about? - January 25, 2024
- How to add Tailwind CSS to Blazor website - November 20, 2023
- How to deploy a Blazor site to Netlify - November 17, 2023